-
State Hackers Exploiting Cisco Zero-Days in Live Networks – ArcaneDoor Breakdown for Blue Teams
Over the past few weeks, Cisco and Microsoft dropped a joint bombshell: a stealthy state-sponsored campaign called ArcaneDoor that’s been flying under the radar since late 2023. What’s wild is…
-
Understanding NIST and ISO 27001: Why Cybersecurity Frameworks Matter
In today’s fast-evolving cybersecurity landscape, organizations need structured frameworks to manage risk, ensure compliance, and strengthen security policies. Two widely used frameworks are NIST Cybersecurity Framework (CSF) and ISO 27001—both…
-
My Journey Through SANS SEC504: How I Prepared, What I Learned, and Tips for the Exam
Taking the SANS SEC504: Hacker Tools, Techniques, and Incident Handling was one of the most challenging yet rewarding experiences of my cybersecurity journey. I want to share my story, not…
-
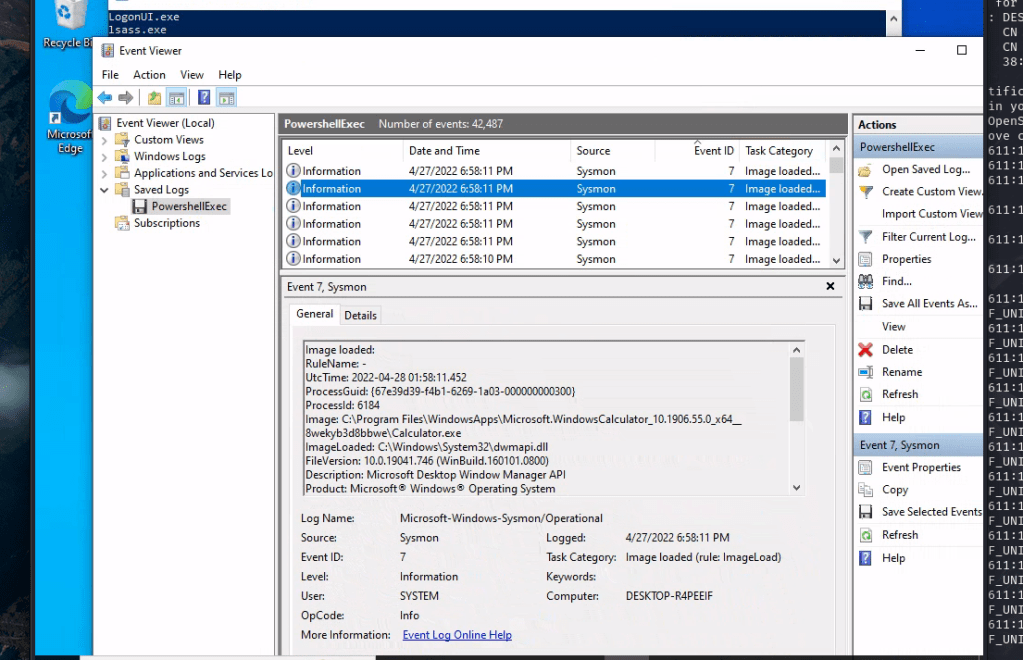
Window event logs Hack The Box, SOC Pathway
Analysing evil with Sysmon and Event Logs Qn: Replicate the DLL hijacking attack described in this section and provide the SHA256 hash of the malicious WININET.dll as your answer. “C:\Tools\Sysmon”…
-
Case Study: How WannaCry Changed the Industry
The Big Hit Imagine a boxer delivering a punch that hits harder than Mike Tyson’s blow to Evander Holyfield. That’s pretty much what WannaCry felt like when it first landed…
-
Security Monitoring and SIEM Hack the box Walkthrough, SOC Pathway.
Introduction To The Elastic Stack Qn: Navigate to http://[Target-IP]:5601, click on the side navigation toggle, and click on “Discover”. Then, click on the calendar icon, specify “last 15 years”, and…
-
Incident handling Hack the Box, SOC Pathway
This is just a quick overview of the topic Incident handling. I hope this walkthrough was useful to you. I decided to make this walkthrough both as a way to…
-
Subscribe
Subscribed
Already have a WordPress.com account? Log in now.